配置salt
这一部分将展示如何配置用户访问,查看和存储job结果,安全性,排错和其它管理任务.
Configuring the Salt Master
Configuring the Salt Minion
Configuring the Salt Proxy Minion
Configuration file examples
Minion Blackout Configuration
Access Control System
Job Management
Managing the Job Cache
Storing Job Results in an External System
Logging
External Logging Handlers
salt.log.handlers.fluent_mod
salt.log.handlers.log4mongo_mod
salt.log.handlers.logstash_mod
salt.log.handlers.sentry_mod
Salt File Server
Git Fileserver Backend Walkthrough
MinionFS Backend Walkthrough
Salt Package Manager
Storing Data in Other Databases
Running the Salt Master/Minion as an Unprivileged User
Using cron with Salt
Use cron to initiate a highstate
Hardening Salt
Security disclosure policy
Salt Transport
Master Tops System
Returners
Renderers配置salt master
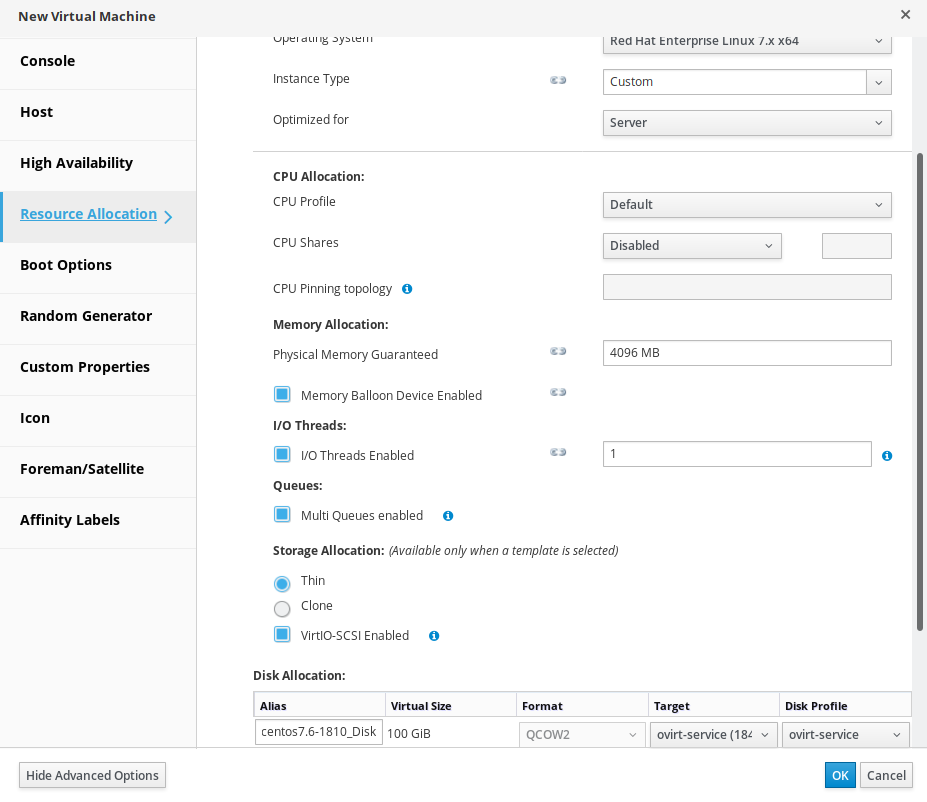
salt系统配置另人惊讶的简单和轻松,两个组件各自有单独的配置文件.salt-master,salt-minion两个文件分别对应两个组件.
默认的salt-master组件的配置文件在/etc/salt/master,FREEBSD显著的不同,位置/usr/local/etc/salt.
主master配置
/etc/salt/master配置文件用来管理salt-master的行为.
约定:被注释的值后面有一个空白行的,表示不需要配置使用默认值.如果没有空白行的表示这个是一个示例,并没有默认值.
1 | 默认的,master会自动包含在master.d/*.conf下的所有配置文件,master.d是一个目录,在master相同的目录级别下. |
minions配置
配置salt-minion非常简单.一般的,惟一需要设置的值是master,这样minion就知道如何定位master.
默认配置文件在/etc/salt/minion,FREEBSE显著不同的,位于/usr/local/etc/salt/minion.